Are Cell Phone Monitoring Apps are really Untraceable on Android?
Most cell phone monitoring and spying apps tout the untraceable aspect of their existence as their winning quality. Which means creepy girlfriends, overbearing parents and neurotic employers could be taking a front row seat to every move you make on your cell phone. Like the idea of someone looking at your emails, pictures, texts, videos, etc? No one does. Luckily the “untraceable” slogan is a lie, regardless of which app you speak of.
Cat and Mouse Games
Being untraceable is a feat that only software for desktop systems can boast about; Google build the Android OS architecture in a manner where it’s impossible for third party apps to hide within a cell phone because they’re shut out of the kernel. To put things in a more simple fashion any OS is split between two parts – the part that works with the user and the part that runs system applications (kernel). The OS for conventional computer systems allows third party developers and software to access the kernel, which handles how system applications interact with the hardware. The kernel is extremely privileged space which is oft misused by many – think birth of a million viruses and spyware. By opening up the kernel to third party developers some great innovations were allowed to breed, but with that bred trouble, too.
The Why in Spy
How is that a problem? For starters, allowing third party access to kernel spells disaster for users for the simple reason that malicious software can easily hide itself by making itself invisible. Files that can harm your system are nowhere for you to find, and hence easily wiggle their way around your data – stealing it, deleting it or even corrupting it. Windows OS can’t restrict third party access to the kernel because several important software won’t be able to run without access to it.
Very Little Space to Hide
However, newer OS like Android don’t allow third party access to their kernel. That divorce of the kernel and user space within the Android OS ensures that all the apps and software installed on a phone are traceable and visible. To figure out if you really are being monitored you can follow a few simple steps. For the purpose of this post I picked up a Samsung Galaxy S1, but the process is more or less the same for most Android phones. We tested the phone out with two apps i.e. StealthGenie and MobileSpy to see whether we could really find them.
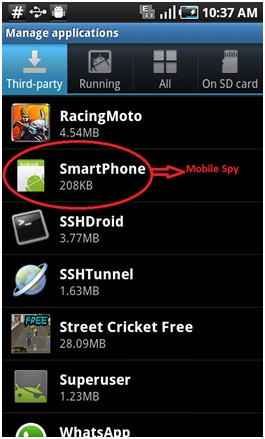
- Start by opening your applications
- Open the settings and tap the manage applications option
- Check to see any apps you don’t recognize and presto you have your monitoring/spy app
Those of you thinking it can’t be that simple: it isn’t. Some apps will allow the installer to pick a fake name and icon for the app when it’s installed so it’s not going to be sitting in that list screaming “I CAN SEE EVERYTHING YOU DO”. But you can still find them. If you click on a suspicious app it’ll lead you to the same result, give or take extremely minor differences. The following are screenshots of the apps once they’re opened:
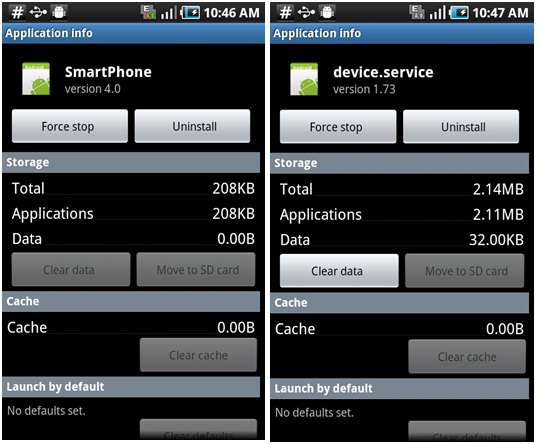
Once you find the app you can shut it down and make sure it doesn’t send over any more of your personal data to anyone. You can then uninstall it. And when you’re done with ridding your phone of all evil you can make sure that you don’t hand it over to anyone without good reason. These apps need to be physically installed on to any phone, they can’t do jack from a remote panel.





1 comment
Rashmi Sinha @ TechInitio
Very nice post. It is good to know that newer mobile phones are secure because we all spend a lot of time with them. Work and personal data are in them and having them protected is very important and i am happy developers know about it.