How to Remove Cerber Virus and Decrypt the Infected files?
The last 2-years haven’t been easy for the cyber security agencies. The rise of different types of Ransomware with all of them performing the same type of dirty work has made life difficult for the Cyber Security Professionals. Millions of dollars have been lost in the last few years at the hands of Ransomware yet we haven’t devised a plan to deal with the upcoming threats. However, while there is nobody denying that there is no consensus on how to deal with all kinds of Ransomware in a similar way, we will present to you a method of dealing with Cerber.
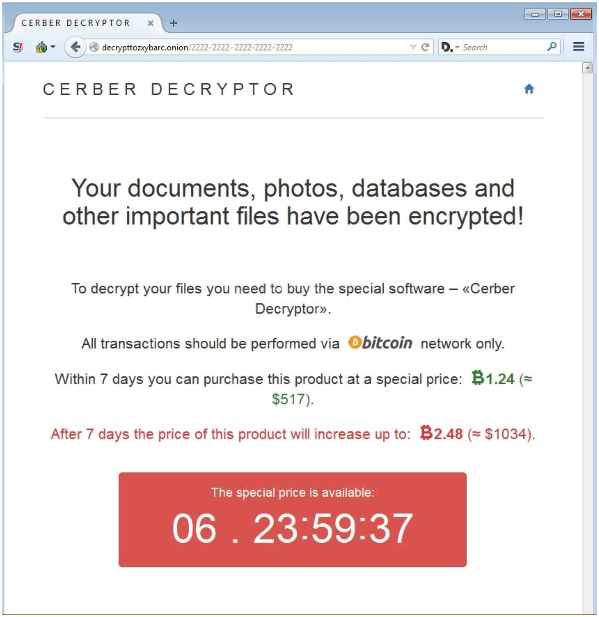
Cerber is no different from its predecessors as it creates 3 files in the computer after encrypting the data. Afterwards, it asks the victim to pay the ransom – which varies in different cases, with a threat of destroying the data if the victim decides to do otherwise.
Thus, if you are the one or know someone who has been disturbed with the shenanigans of Cerber, below mentioned are some of the methods to decrypt your useful data …
How Cerber Penetrated through and Infected Your Computer
Similar to a technique that has been epitomized by the authors of Malware in the past few years, Cerber uses a spam email which contains an attachment, to penetrate into your computer. If the user wants to turn him/her into a victim, they would open the file and that will be equivalent to handing over the keys of your home to a robber.
As you might guess, once a user does it, there is simply no way back because of the execution and running speed of Cerber. The Antivirus that are installed on your computer has a very remote chance to catch Cerber because it constantly modifies its appearances.
What to do if your system has been infected with Cerber?
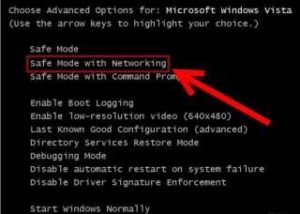
First of all, you don’t need to panic as it would only aggravate the matters. Secondly, you are ought to start your computer in a safe mode. In order to start your computer in safe mode, the following are the few steps that you need to follow.
- Restart the computer using normal way
- Before the system starts again, hit f8
- This F8 will lead you towards a screen with the title of “Advanced Boot Options”. Here, there will be a myriad of menu bars. Click on the one which is titled as “Safe Mode with Networking”
Now that you have entered into your computer in a safe mode, open the internet browser and download an antivirus with which you have worked before and is reliable. Scan the entire computer, no matter how much time it takes. At the end of the scan, you will see that the antivirus would have listed some threats. Delete ALL of them.
If you are unsure about the antivirus which would detect the entries of Cerber, download the below mentioned removal tool
How to remove files and folders of Cerber
After Cerber had infected your computer, it is likely that it would have created entries and files. Therefore, it is necessary for you to MANUALLY remove them all.
Following are the entries that you need to remove from Registry.
HKCU\Control Panel\Desktop\SCRNSAVE.EXE "%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\{randomname}.exe"
HKCU\Software\Microsoft\Command Processor\AutoRun "%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\{randomname}.exe"
HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run "%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\{randomname}.exe"
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\{randomname} "%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\{randomname}.exe"
HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce\{randomname} "%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\{randomname}.exe"
After removing the aforementioned entries, also remove the files with the following names/extensions …
%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\{randomname}.exe
How to decrypt the files that have been encrypted by Ransomware?
There are four ways you could decrypt the files. All of them have been mentioned below …
Use an automated Encryption tool
Luckily for us Computer users, reliable Cyber Security Giants like Kaspersky has developed Ransomware decryptor over the years. As suggested by its name, the Kaspersky Ransomware detector would decrypt all the files that have been encrypted by Cerber.
How to manually delete .cerber files
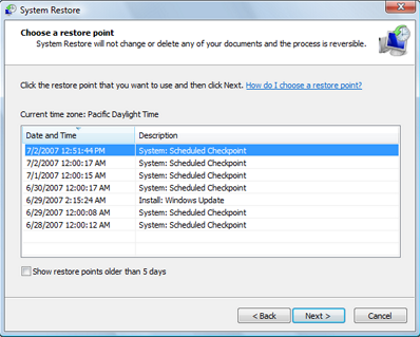
If you use Windows 8 or higher operating system, slide your cursor to the top left side and a black box will appear. Thereon, search for “System Restore”. For all the previous versions of the windows, go to the start menu and search for the same.
After you have found the whereabouts of system restore, start the search. Click on the result and follow the instructions that appear on your screen to proceed.
Activate the previous version of the files

In case the Windows Backup is active on your computer, it would have made copies of all the files and folders that are present in your device. Thus, as you might guess, you could utilize this option to get back the files and folders that have been modified or destroyed by Cerber.
For any file that you choose to restore, right click on it and then click on the “Properties”. There you will find a tab with the name of “Previous Version”. Here, select the latest version and then select “Copy”. Finally, Click “Restore”.
Restore using shadow copies
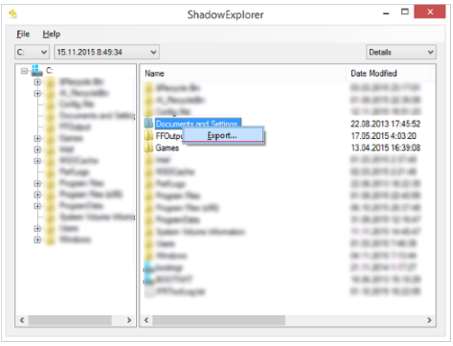
As evident from the aforementioned screenshot, you need to download and run Shadow Explorer. Afterwards, click on the folders where Cerber has attacked and then select export to restore the files.
How to Protect your Computer with HitmanPro

Even though you could be of the view that your antivirus is the best in the world, I would suggest you go for HitmanPro.Alert. This is a very famous malware scanner and would shield your system from Ransomware attacks.
Hope these tips will help you to remove .cerber ransomware from your computer.
[Source]