Exactly what it sounds like: Why the Ping of Death needs to be prevented, and how to do so
With all the attention distributed denial of service (DDoS) attacks are now getting for being big bad horrible things, you have to wonder if the security specialists who named the different attack types didn’t miss out on some opportunities. The Smurf Attack, for instance, sounds like something that would tickle your kneecaps, not like something that could dummy a website and hurt a business, and the Slowloris just sounds like an animal that likes to cuddle.
Whoever named the Ping of Death nailed it, however. Not only does the first part of the name give you an idea of how it works, but the tail end tells you what your website is in for if you get lined up in the crosshairs of this DDoS attack.
Improper protocol
DDoS mitigation provider Incapsula defines the Ping of Death as a distributed denial of service attack in which attackers seek to freeze, crash or destabilize the targeted website or online service by using a simple ping command to send malformed or oversized packets.
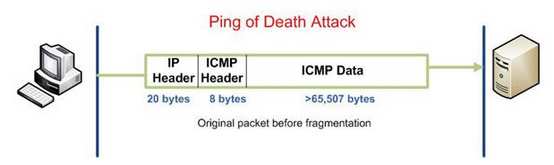
A ping is a network utility that sends an Internet Control Message Protocol or ICMP echo request packet to determine 1) if a host is reachable and 2) how long it takes to be reached. When the host receives the echo request, it responds with an echo reply.
The size of an ICMP echo request packet is no larger than 65,535 bytes because sending a ping packet any larger would be a violation of Internet Protocol. And therein lies the Ping of Death attack. To circumvent this size limit, attackers send fragments of malformed, oversized packets that the target attempts to assemble. When the attack is successful, the oversized packets cause memory overflow which leads to an unavailable host for legitimate users.
The ping appeal
Ping of Death is what’s known as a protocol attack because it violates Internet Protocol. Protocol attacks are notoriously difficult to defend against because these protocols are necessary for the internet to operate the way it should, so simply blocking the entire protocol in order to block the attack traffic is not an option.
Attackers are drawn to Ping of Death attacks because not only are they hard to defend, but they’re also relatively easy to launch – the only information an attacker has to have on a target is its IP address.
Life after death
A distributed denial of service attack isn’t like, say, stubbing your toe on a table leg, hobbling around for a couple of seconds amidst a flurry of swear words, and then continuing on to the kitchen like nothing happened once the pain has passed. It isn’t just bad while it’s happening. A DDoS attack is more like a concussion. There’s the initial hit, which is bad enough, but then the effects of it linger.
The first consequence of DDos attacks, Ping of Death included, is an unavailable website or service as well as the associated money spent dealing with an unmitigated attack, which for a sizable organization can ring in at $40,000 per hour.
Dealing with the aftershocks of an attack can be just as trying, with many attacks causing hardware or software damage, or being used as a smokescreen for a data intrusion that compromises customer information or intellectual property. Intrusion or not, affected websites and companies often suffer a loss of loyalty from users as well as a feeling of distrust – a feeling that may be even more pronounced when it comes to Ping of Death attacks.
A legacy of pain – and how to prevent it
The Ping of Death is an attack that exploits legacy weaknesses in target systems. In other words, weaknesses that should have already been patched, hence the amplified feeling of distrust that may accompany a successful attack. This isn’t all website-owner error, however. Ping of Death attacks have been known to find vulnerabilities even major corporations don’t know about, such as in the case of this summer’s IPv6 debacle when a wide range of operating systems from major players like Cisco and Juniper were found to be vulnerable to these attacks through a process by the name of Neighbor Discovery.
The first step in preventing the Ping of Death is making sure all systems are updated and patched. The second step is finding a way to deal with all protocol attacks, which means investing in professional DDoS mitigation that inspects traffic at a granular level in order to selectively block oversized packets – even if they’re fragmented – as well as malicious traffic that can accompany other types of protocol DDoS attacks. This approach allows legitimate traffic through to the website unimpeded while attack traffic never reaches the website.
With the proper preventative measures in place, you could transform the accurately named Ping of Death into the even more accurately named Dead Ping of Death. An appealing prospect, no doubt. RIP.