What Are the Two Main Roles of Proxy Servers?
Whether you’re an individual or a business, proxy servers have a multitude of purposes. They help protect against cybercrime, monitor internet use, and more.
For businesses, a proxy can help protect their intellectual property by preventing hackers from accessing company data. In addition, proxies can act as firewalls and filters to protect endpoints from malware threats.
Acting as a Mediator
In mediation, a neutral third party helps resolve disputes by facilitating communication and encouraging parties to reach agreements. Mediation is a voluntary, non-binding process.
Mediation can help resolve conflict and improve the quality of life in communities. It is gaining popularity in solving disputes informally and outside of court.
It can be used to settle business and labor disputes. It is also often used in divorce cases and other family matters.
A mediator can help people in a dispute understand why they are having problems. They can also help them understand their own interests and those of the other person or party.
Mediators must be skilled in the art of dialogue and empathy, which are essential skills for successful mediation. They may need specialized training or certification in the subject matter of their work.
Acting as a Cache
A cache is a resource that stores HTTP responses that subsequent requests to the same target URI can reuse. It can be used to store a wide variety of representations, including 200 (OK) responses, permanent redirects, negative results (e.g., 404), incomplete results (e.g., 206), and responses to other methods if their definitions allow caching.
The most common cache entry is a successful GET request to a targeted URI that yields a 200 (OK) response, but it can also be used for other requests, such as a 206 (Partial Content) or a 404 response, when appropriate.
Caches can use a heuristic to determine the current age of a stored response; if the cache does not find an expiry value for the response, it can add an explicit value to the current_age field to indicate that the stored response is already stale.
A cache MUST NOT store a stale response unless the origin server specifies an expiry time for the response in an explicit in-protocol directive. In addition, a cache MAY use a heuristic to determine an expiry time if it can do so reliably.
Acting as a Filter
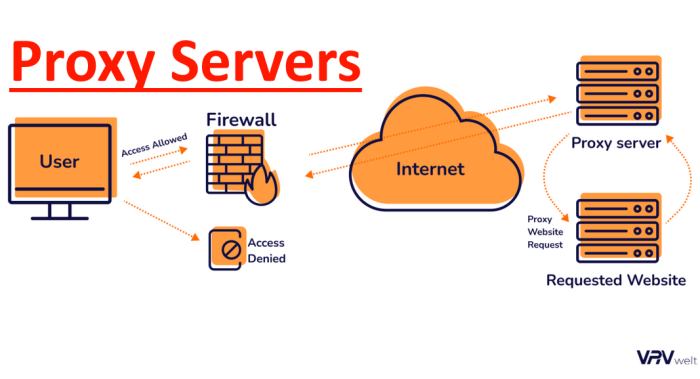
A proxy service acts like a firewall between your computer and the internet. It examines the data going in and out of your device to help prevent hackers or other bad actors from gaining access to your digital identity.
Proxies also allow individuals and organizations to increase their privacy by concealing their IP addresses while browsing the internet. Some proxies can even change their geographic location, providing full anonymity while browsing the web.
A proxy can also be used to bypass government censorship or content restrictions. For example, if you are a fan of a local sports team and the team’s games are blacked out in your area, you can use a different location proxy to log into a website from the other side of the country and watch the game.
Acting as a Reverse Proxy
A reverse proxy server sits in front of a web server, intercepting requests from clients and routing them to and from the origin server. This makes it much harder for hackers to gain access to your servers and launch direct-to-IP denial-of-service attacks.
Reverse proxies are also useful for load-balancing traffic and distributing requests among multiple origin servers. This can reduce the distances that requests need to travel and improve performance, especially when using a CDN.
A reverse proxy can also protect users by monitoring and filtering user traffic, including encrypted data, as well as inspecting traffic destined for managed resources. This helps ensure that only approved apps and services are being used, which protects against SQL injection, cross-site scripting, and other security threats.