Booters and Stressers: What you need to know about DDoS for hire?
Think back to when you were a kid. No matter how well-adjusted and even-tempered you were (or weren’t) there was at least one other kid you just could not stand. You hated his face, his hair, his teeth, the way he talked, the way he looked at you, and the way he just existed. Remember the way he’d eat his sandwiches? He ate his sandwiches like a jerk.
Chances are, though, that no matter how much you couldn’t stand him, you didn’t go marching over to throw a dozen eggs at his house. The chances of getting caught were too high. You’d get in trouble. Everyone would know you did it and your parents would be mortified.
But what if there had been a machine you could have secretly put a dollar in from several blocks away, and it would have rolled up in front of that kid’s house and started firing eggs? All that mess and damage, with none of your fingerprints on the eggshells. It would have been a strong consideration, right? That business model all grown-up is how a group of people running services called Booters or Stressers are making a pretty sweet little profit offering DDoS attacks for hire.
DDoS and Booter basics
DDoS is the acronym for a distributed denial of service attack, which is so named because it denies the use of a website and its services to legitimate users by suspending or disrupting the services of an internet-connected host. Booter services – which is a term that can be used interchangeably with Stresser services –offer DDoS attacks to anyone willing to pay for them.
With a Booter, users typically pay a fee and are given access to a user-friendly platform from which they can choose their target and get to DDoS-ing. To give you an example of the cost-friendliness of this lovely service, one sample Booter charges $40 USD/month for an unlimited number of DDoS attacks lasting one hour.
What DDoS can do?
The main area where the egg-firing machine analogy falls apart is in the potential damage. Even with a super-powerful egging machine, the worst possible damage is probably a broken window. But a DDoS attack? One hour of a DDoS attack can cost an organization $40,000. That’s not even mentioning the software or hardware damage that can be done, the IP theft, financial data theft, loss of revenue and loss of consumer trust that can happen.
In order to inflict damage, a would-be DDoS attacker with access to a Booter service doesn’t even have to unleash the attack. DDoS ransom notes where someone demands a set amount of money in exchange for not hitting that website with a DDoS attack are becoming increasingly common.
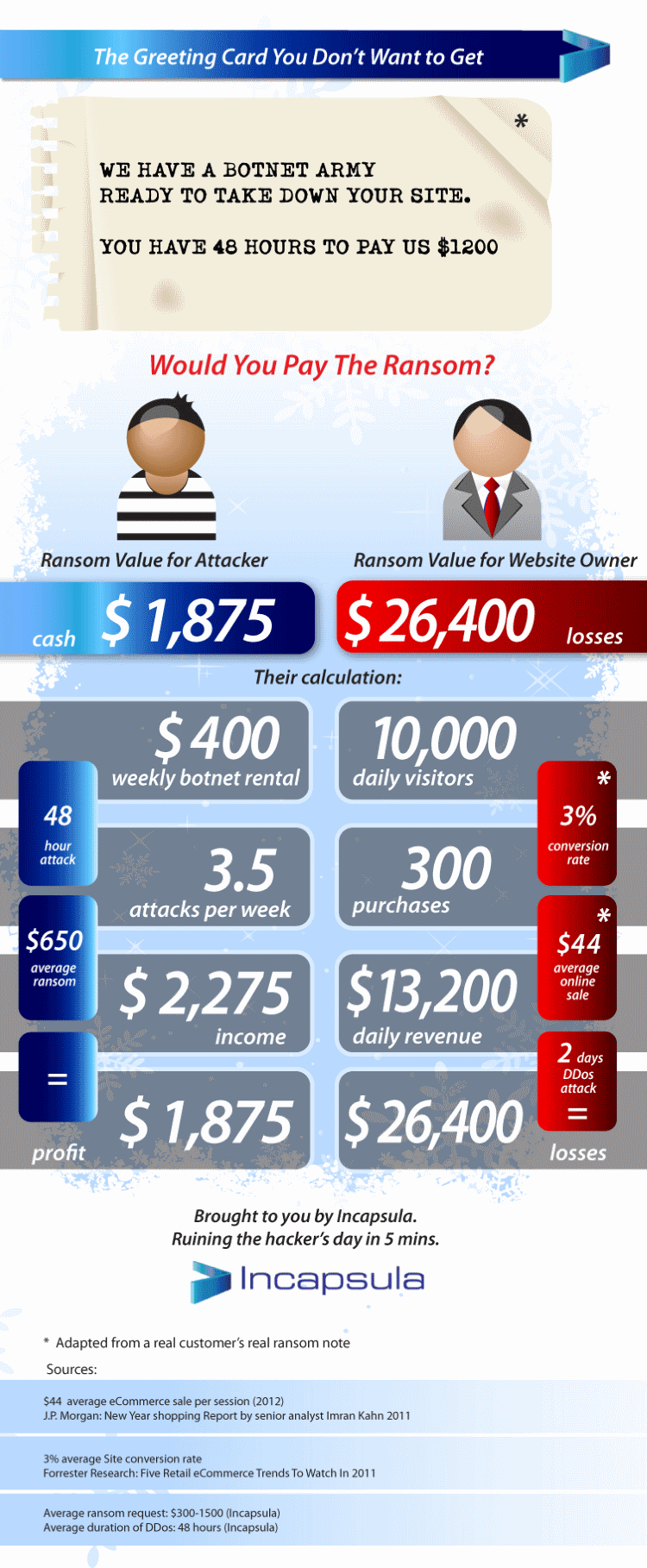
Ransom note – potential damage for website and potential profit for attacker
(Source + Hi-Res image: Incapsula)
Who does that?
DDoS attacks are wildly common, and Booter services are popular enough that there are plenty of them online with their numbers always growing. That begs the question: who is it that’s using these websites?
The answer is depressing because your website could potentially be made a target by just about anyone. Business rivals are an obvious choice, but when you factor in the chance to make fast money from a DDoS ransom note, your potential attacker net widens considerably. Kids who don’t know who you are and have never visited your website before might be keying your url into a Booter.
While many Booter-for-hire users are unsurprisingly gamers who pay the Booter fee in order to DDoS Minecraft servers and similar websites, there have been some high profile attacks from the people behind these services. The Lizard Squad, famous for their attacks on Sony Playstation Network and Microsoft’s Xbox Live, claimed those major attacks were simply advertisements for their Booter service.
Could a Booter get to your website?
DDoS attacks have been found to affect 45% of organizations – that’s very nearly 1 in 2. And with Booter services and DDoS ransom notes gaining popularity, that number could very well rise. If you’re considering whether or not you should look into professional DDoS mitigation, and you haven’t yet decided that you absolutely should, consider this: you could pay for months of DDoS protection with what you might end up paying in a single ransom.
It isn’t nice to think that your website could fall victim to a DDoS attack. It’s even worse to think that the attack might come from someone hiding behind a Booter. While you ultimately may not have plugged a dollar into that egging machine due to your own principles, there are plenty of people out there who don’t mind being cowardly in order to unleash a DDoS attack or make a quick buck on a ransom note. That’s the reality your website is living in.